Scan images in a Kubernetes cluster
This feature was deprecated in Calico Cloud version 21.1.0 and will be removed in a future release. Availability depends on when you started using Calico Cloud.
- For users who started using Calico Cloud in April 2025 or later, this feature is not available.
- Legacy users, who started using Calico Cloud before April 2025, can continue to use this feature until it is removed in a future release.
Scan all images in a Kubernetes cluster for vulnerabilities to achieve a continuous clean bill of health and defense in depth.
Common use cases for scanning in a Kubernetes cluster are:
- Images may pass scanning during the build phase, but they could contain vulnerabilities days or weeks later
- Third-party images that are pulled from public registries are often not scanned in build pipelines and can contain Critical or High vulnerabilities
- Application teams may build one-off images outside of their pipeline to make an emergency patch and fix a critical bug.
About Image Assurance scanner
The Image Assurance scanner that runs in a Kubernetes cluster is out-of-the-box ready to use without configuration. It runs as a daemonset in a managed cluster where images are located, and is installed on all nodes in the cluster.
Vulnerability detection consists of these steps:
- Image Assurance scanner - generates a dependency list Software Bill of Materials (SBOM) using Syft
- Vulnerability lookup - Calico Cloud uploads the SBOM where packages are matched with known CVEs in the vulnerability databases based on dependencies using Grype
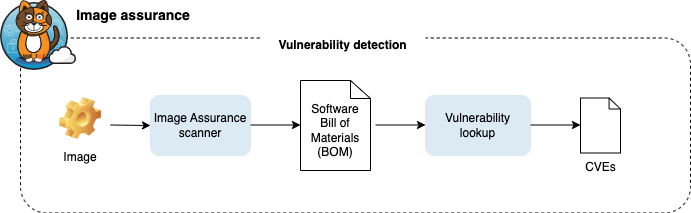
Calico Cloud checks running images for new vulnerabilities every 24 hours and reports scan results to the Image dashboard in the web console.
Before you begin
Unsupported
- OpenShift
- GCP-Kubeadm
- AWS-Kubeadm
- GKE
Cluster requirements
- Containerd is the container runtime
- AKS clusters: if you are using Kubernetes v1.19 or higher, containerd should be your default runtime
- Containerd must be using overlays or native file system snapshotter
How to
Get latest version of Image Assurance
- On the Managed Clusters page, select the cluster from the list, and click Reinstall.
- Copy the updated installation script command and run it against your cluster.
Enable scanner
Complete the following steps for each managed cluster you want enabled with the cluster scanner:
-
Modify the Image Assurance installation resource.
kubectl edit imageassurance default -
Set the
clusterScannerfield toEnabledand save the file.
The cluster scanner is deployed as a container inside the tigera-image-assurance-crawdad daemonset.
- Verify that a new container with name,
cluster-scanneris created inside the daemonset.
That’s it. The cluster scanner will start scanning images on running pods in the cluster. For help viewing image events in the web console, see View scanned and running images.
Customize scanner settings
To change default settings, modify the Image Assurance installation resource.
-
Container runtime socket path
Set the
criSocketPathfield to the path of the container runtime socket. Default:/run/containerd/containerd.sock -
Containerd file system root path
Set the
containerdVolumeMountPath. Default:/var/lib/containerd/.
Configure exclusions for image scanning
To specify which namespaces should be excluded from future scans, follow the following steps.
- Modify your Image Assurance installation resource to include the
exclusions.namespacesfield. List each namespace you want to exclude.
apiVersion: image-assurance.operator.tigera.io/v1
kind: ImageAssurance
metadata:
name: default
spec:
clusterScanner: Enabled
exclusions:
namespaces:
- "kube-system"
- "dev-qa"
In this example, the workloads in the kube-system and dev-qa namespaces are excluded from future image scans.
Applying or updating namespace exclusions affects only future scans. Results from scans conducted prior to these exclusions will remain unchanged. The exclusions configured will apply to both cluster scanner and runtime view (Running Images tab).
Disable scanner
- Modify the
imageassuranceinstallation resource.
kubectl edit imageassurance default
- Set the
clusterScannerfield toDisabledand save the file. This deletes the cluster scanner container from the daemonset from your cluster.