Enable policy recommendations
Big picture
Use policy recommendations to automatically isolate namespaces with network policy.
Value
One of the best practices for improving the security posture of your Kubernetes cluster is to implement namespace isolation with network policy. Namespace isolation helps to implement a zero-trust and least-privileged security model, where only required communication between namespaces is authorized and everything else is blocked. This helps mitigate the risk of lateral movement within a cluster in the event of an attack.
Calico Cloud makes it easy for platform operators to implement namespace isolation without experience in authoring network policy or detailed knowledge of how application workloads are communicating. Calico Cloud analyzes the flow logs that are generated from workloads, and automatically recommends and stages policies for each namespace that can be used for isolation.
Before you begin
Unsupported
- Windows nodes
Required RBAC
To enable/disable and use policy recommendations, you must have the tigera-network-admin role or permissions to update, patch, get, list, watch projectcalico.org resources:
- tiers
- policyrecommendationscopes
- stagednetworkpolicies
- tier.stagednetworkpolicies
- networkpolicies
- tier.networkpolicies
- globalnetworksets
Specifically, you will need access to the namespace-isolation tier and to staged and network policies in the namespace-isolation tier.
Recommended
Basic knowledge of policies in the web console and tiers:
Limitations
Creating and managing policy recommendations is available only in the web console.
How to
- Enable policy recommendations
- Activate and review policy recommendations
- Review global settings for workloads
- Update policy recommendations
- Private network recommendations
- Troubleshoot policy recommendations
- Disable the policy recommendations feature
Enable policy recommendations using the web console
- In the left navbar in the web console, click Policies, Recommendations.
- On the opt-in page, click Enable Policy Recommendations.
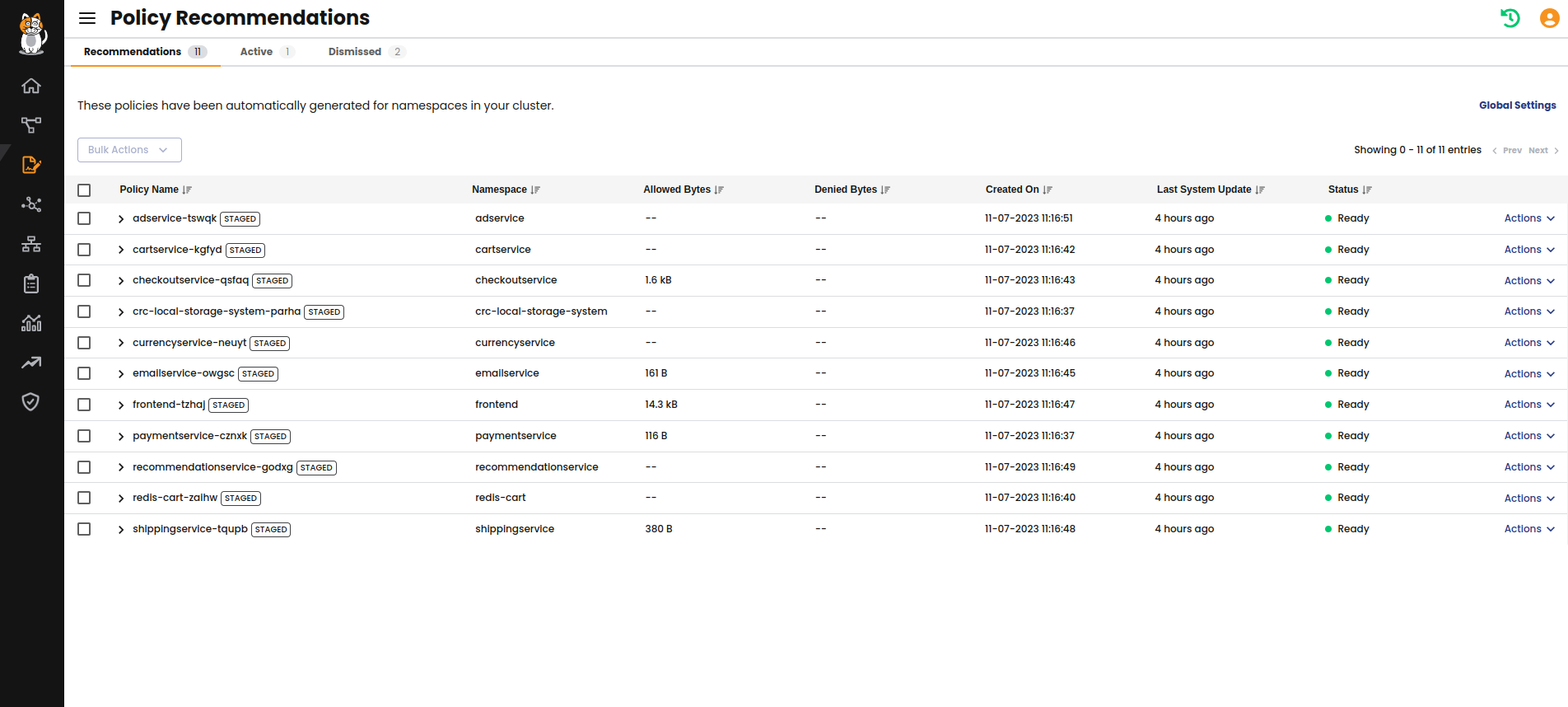
The Policy Recommendations board is automatically displayed.
Notes:
- A policy recommendation is generated for every namespace in your cluster (unless namespaces are filtered out by an Admin using the selector in the PolicyRecommendationScope resource).
- Flow logs are continuously monitored for policy recommendations.
- Recommended policies are continuously updated until you Add to policy board or Dismiss policy using the Actions menu.
- Policy recommendations are created as staged network policies so you can safely observe the traffic before enforcing them.
- Traffic originating from the recommended policy's namespace is used to generate egress rules, and traffic destined for the namespace is used to define ingress rules.
- To stop policy recommendations from being processed and updated for a namespace, click the Action menu, Dismiss policy.
Enable policy recommendations using kubectl.
To enable the policy recommendations feature, set the RecStatus parameter to Enabled, in the Policy recommendations resource.
kubectl patch PolicyRecommendationScope default --type='json' -p='[{"op": "replace", "path": "/spec/namespaceSpec/recStatus", "value": "Enabled"}]'
Activate and review policy recommendations
Policy recommendations are not enabled until you activate them and move them to the Active board.
From the Policy Recommendation board, select a policy recommendation (or bulk select) and select, Add to policy board. Click on the Active tab.
You can now view the activated policies in the Policies Board. In the left navbar, click Policies.
Policy recommendations are added to the namespace-isolation tier. Note the following:
- Staged network policy recommendations work like any other staged network policy.
- You cannot move recommended staged policies in the
namespace-isolationtier. - The name of the
namespace-isolationtier is fixed and cannot be changed
You are now ready to observe traffic flows in Policies board to verify that the policy is authorizing traffic as expected. When a policy works as expected, you can safely enforce it. See Stage, preview impacts, and enforce policy for help.
Review global settings for workloads
The default global settings for capturing flows for policy recommendations are based on application workloads with frequent communication with other namespaces in your cluster.
Global settings are found on the Policy Recommendations board, Action menu.
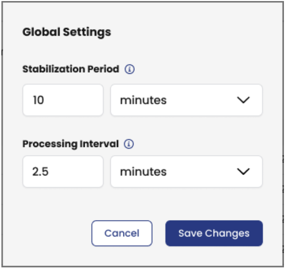
-
Stabilization Period is the learning time to capture flow logs so that a recommendation accurately reflects the cluster's traffic patterns.
-
Processing Interval is the frequency to process new flow logs and refine recommendations.
For application workloads with less frequent communication, the stabilization period setting may not be long enough to get accurate traffic flows, so you’ll want to increase the time. We recommend that you review your workloads immediately after you enable policy recommendations and adjust the settings accordingly.
Changes to all other policy recommendations parameters require Admin permissions and can be changed using the Policy recommendations resource.
Update policy recommendations
This section describes common changes you may want to make to policy recommendations.
Relearn activated recommendations
As new namespace and components are added to a cluster, your activated policy recommendation may need to be updated to reflect those changes. If a policy recommendation has not been enforced, you’ll need to update it to allow traffic.
- On the Policies Recommendations board, click the Active tab, which lists the active staged network policies.
- Select the Actions menu associated with the policy in question, and click Dismiss policy.
- Click the Dismissed tab, select the Actions menu, and Reactivate the policy.
Rerun policy recommendations for an enforced policy
To generate a new recommendation for an enforced policy, delete the network policy on the Policy board.
Stop policy recommendation updates for a namespace
- On the Policy Recommendations board, click the Recommendations tab, which lists the recommendations.
- Select the recommendation, click the Actions menu, and click Dismiss policy.
To reactivate a policy recommendation for a namespace, select the dismissed staged policy, and from the Actions menu, select Reactivate.
Private network recommendations
If any flow to a private network in your cluster is found, a private rule is automatically created that contains RFC 1918 subnets, which will allow traffic to/from those endpoints. If you need to apply a more restrictive approach, create a GlobalNetworkSet and update it with the desired CIDR blocks. The recommendation engine will identify flows to your private IPs and generate the appropriate NetworkSet Rule.
Notes: Exclude any CIDR ranges used by the cluster for nodes and pods.
Troubleshoot policy recommendations
Problem: I’m not seeing policy recommendations on the Policy Recommendations board.
Solution/workaround: Policy recommendations are based on historical flow logs that match a request, and are generated only for flows that have not been addressed by any other policy. As such, there are times when policy recommendations will not be generated:
-
Not enough traffic history
If you recently installed Calico Cloud, you may not have enough traffic history. Workloads must run for some time (around 5 days) to get “typical network traffic” for applications.
-
Traffic is covered by existing policy
Even if your cluster has been running for a long time with traffic, the flows may already be covered by existing policies.
To verify why there may not be any recommendations, follow these steps:
- Go to Service Graph, Default.
- Filter flow logs for your namespace.
- Investigate the content within the
policiesfield for the flow logs in question. - Validate that no other enforced policy already addresses the flow.
Problem: Why are egress-to-domain rules being generated for a Kubernetes service?
Solution/workaround: The policy recommendation controller can only read the cluster domain of the cluster it runs in. If you have managed clusters with a non-default domain (cluster.local), the controller will treat egress traffic as though it is to a domain.
Disable policy recommendations
To disable the policy recommendations feature, set the RecStatus parameter to Disabled, in the Policy recommendations resource.
kubectl patch PolicyRecommendationScope default --type='json' -p='[{"op": "replace", "path": "/spec/namespaceSpec/recStatus", "value": "Disabled"}]'
When disabled, non-active staged policies in the Policies Recommendations board are no longer updated. Existing activated and enforced staged network policies are not affected by disabling policy recommendations.