Container threat detection
Compliance reports are deprecated and will be removed in a future release. We're building a new compliance reporting system that will eventually replace the current one.
Big picture
Get alerts when security threats, such as malware and other suspicious processes, are detected in your cluster.
Value
Calico Cloud provides a threat detection engine that analyzes observed file and process activity to detect known malicious and suspicious activity.
As part of these threat detection capabilities, Calico Cloud maintains a database of malware file hashes. This database consists of SHA256, SHA1, and MD5 hashes of executable file contents that are known to be malicious. Whenever a program is launched in a Calico Cloud cluster, malware detection generates an alert in the Security Events Dashboard if the program's hash matches one that is known to be malicious.
Our threat detection engine also monitors activity within the containers running in your clusters to detect suspicious behavior and generate corresponding alerts. The threat detection engine monitors the following types of suspicious activity within containers:
- Access to sensitive system files and directories
- Command and control
- Defense evasion
- Discovery
- Execution
- Impact
- Persistence
- Privilege escalation
Before you begin...
Required
Calico Cloud Container threat detection uses eBPF to monitor container activity, and it runs on Linux-based nodes in a Kubernetes cluster.
Nodes require amd64 (x86_64) architecture CPUs and one of the following distributions:
- Ubuntu Bionic with kernel version 4.15.0 or 5.4.0
- Ubuntu Focal with kernel version 5.4.0, 5.8.0 or 5.11.0
- CentOS 7 or 8
- Fedora 29, 30, 31, 32, 33 or 34
- Amazon Linux 2
- Debian Stretch or later
- Any other distribution with a Linux kernel 5.0 or later that provides BPF Type Format (BTF) for that kernel at the standard place (/sys/kernel/btf/vmlinux)
If your nodes are running a variant kernel, or a similarly-modern kernel but with another platform, please open a Support ticket so we can bundle the BTF data to precisely match the version of the kernel running on your cluster nodes.
How to
- Enable Container threat detection in the managed cluster
- Monitor the Security Events page for malicious programs
- Exclude a process from Security Events alerts
- Update detectors settings
Enable Container Threat Detection
Container threat detection is disabled by default.
To enable Container threat detection on your managed cluster, go to the Threat Defense section in the Calico Cloud UI, and select Enable Container Threat Detection. This will result in Container threat detection running on all nodes in the managed cluster to detect malware and suspicious processes.
Alternatively, Container threat detection can be enabled using kubectl:
kubectl apply -f - <<EOF
apiVersion: operator.tigera.io/v1
kind: RuntimeSecurity
metadata:
name: default
EOF
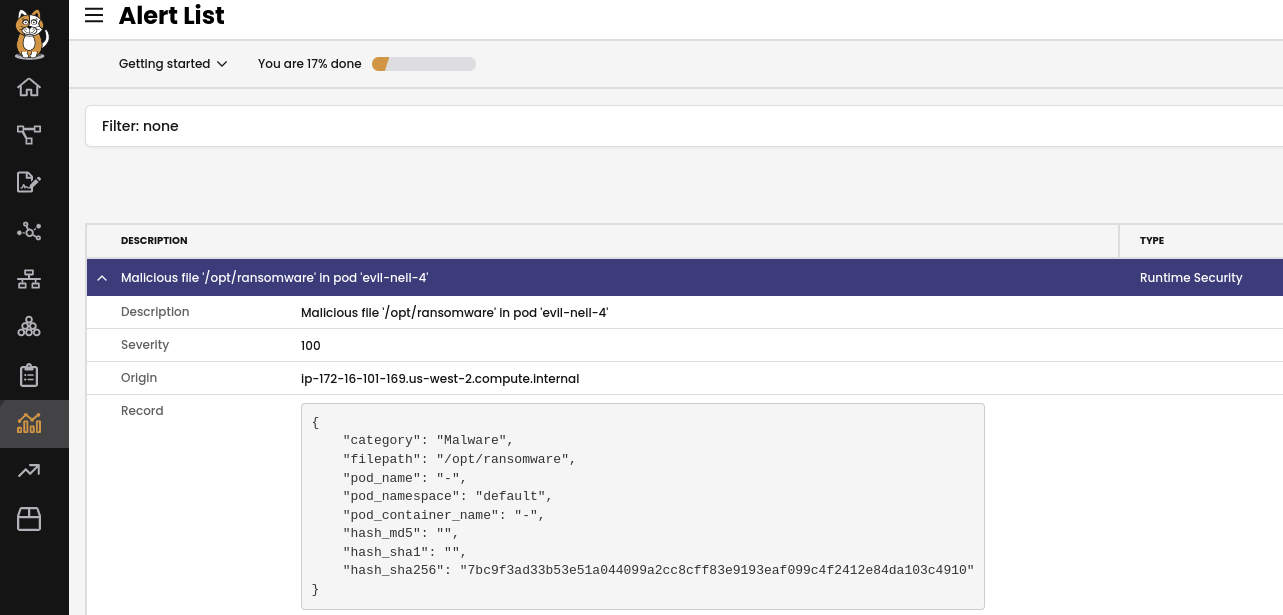
Monitor the Security Events page for malicious programs
If a malicious or suspicious program is run within the cluster, it will be reported on the Security Events page of the Calico Cloud UI.
Exclude a process from Security Events alerts
You can turn off Security Events alerts for processes in your cluster that you know to be safe.
To create an exception, add the process to the Runtime Security resource with kubectl:
kubectl apply -f - <<EOF
apiVersion: operator.tigera.io/v1
kind: RuntimeSecurity
metadata:
name: default
spec:
runtimeExceptionList:
- matching: Exact
processInvocation: "runc init"
namespace: default
- matching: Regex
processInvocation: "\b(shred|rm|mv).*((bash|ash|zsh|fish|fish_read)_history|history)\b"
EOF
The matching field can take one of two values: Exact or Regex.
Setting the matching field to Regex allows you to pass a regular expression to capture more than one value for each field. Whereas Exact would require each field to be an exact match.
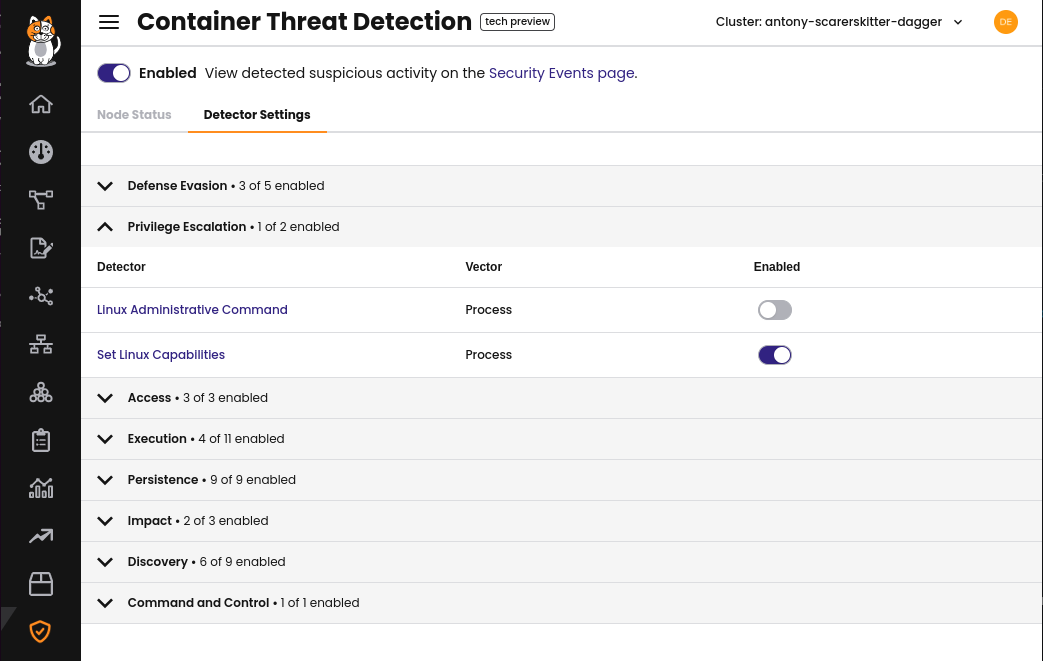
Update detectors settings
Threat detection capabilities are provided by detectors that protect against specific MITRE techniques. Detectors are grouped by the MITRE tactics they protect against. Additional information for each detector can be found by clicking on a detector. All detectors are enabled by default, with the option of disabling specific detectors if needed.
Configure detectors via RuntimeSecurity Custom Resource
Detector settings configured through the UI are stored in the cluster's RuntimeSecurity custom resource. When configuring multiple clusters, the same configuration can be applied to all clusters.
Get the reference detectorsConfig:
detectorConfig="$(kubectl get runtimesecurities.operator.tigera.io default -o jsonpath="{.spec.detectorsConfig}")"
Container Threat Detection can be enabled with the desired configuration in a single command:
kubectl patch -n tigera-runtime-security runtimesecurities.operator.tigera.io default --type='merge' -p="{\"spec\":{\"detectorsConfig\": $detectorsConfig}}"
Container activity logs in Kibana
Lower-level reports for file and process activity are captured for your cluster in Kibana using the index pattern tigera_secure_ee_runtime*.
Please note that most of these reports are not usually malicious; they constitute the raw data against which known malicious program fingerprints and activity patterns are compared. Suspicious and known malicious activity is reported on the Security Events page of the Calico Cloud UI.