Security Posture Overview dashboard
This feature is tech preview. Tech preview features may be subject to significant changes before they become GA.
Big picture
View the overall security posture of your Kubernetes cluster and use a prioritized list of recommended actions to improve your security score over time.
Value
Is the security posture of your cluster getting worse or better over time? Do your stakeholders ask for evidence that you are addressing security issues and showing improvement?
The Security Posture Overview dashboard allows every team no matter how small, to measure the security posture of their cluster and take steps to reduce risk over time. Because the dashboard is based on existing Calico Cloud data, no configuration is required. You can start improving the security posture of your Kubernetes cluster from day one.
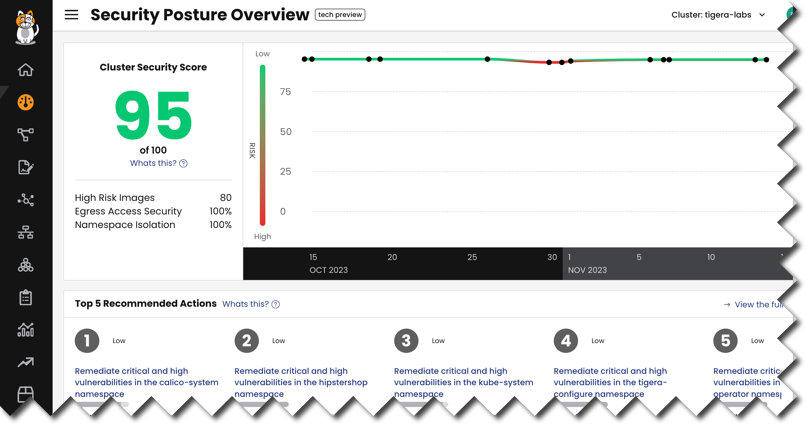
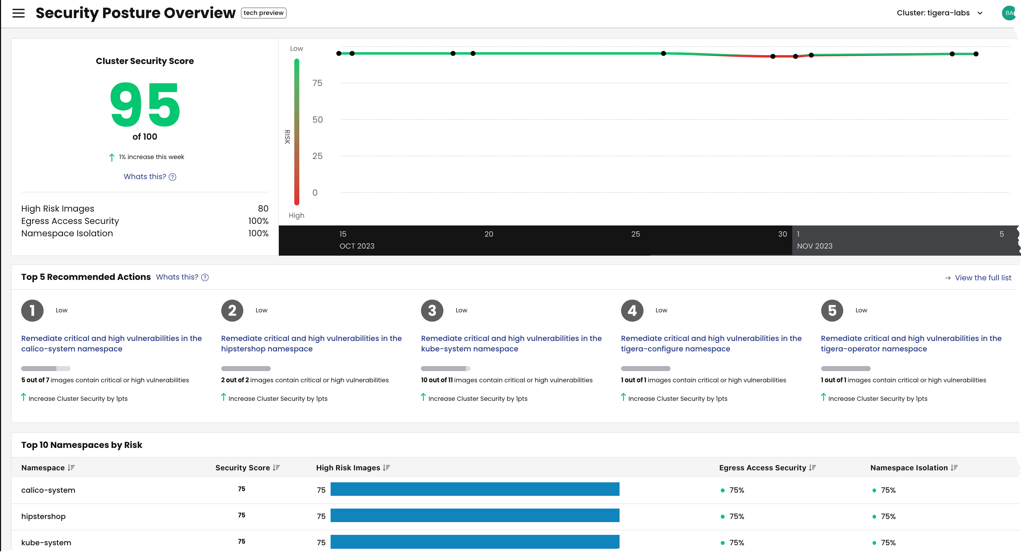
The Calico Cloud Security Posture Overview dashboard in Manager UI provides:
- An overall Security Cluster Score that measures the following aspects of security posture management:
- Namespaces are isolated with a network policy
- Running images do not contain critical or high vulnerabilities
- Running images have been scanned for vulnerabilities
- Egress access to destinations outside the cluster have been secured with network policy
- A prioritized list of Recommended Actions to improve the score
- A summary of top 10 namespaces by risk
Concepts
Security posture management
Security posture management for Kubernetes is the secure configuration of the control plane, applications, and other resources to reduce risk and prevent security events from happening. For each cluster that you connect to Calico Cloud, we calculate a Cluster Security Score based on several risk types and measure its security posture.
Scoring frequency
By default, Calico Cloud automatically runs risk calculators on every managed cluster approximately every 24 hours.
Before you begin
This feature is currently part of an active Beta program and will include significant changes and improvements based on user feedback. If you would like to participate, please reach out to your Customer Success representative.
Limitations
-
The current bias of the dashboard is to include the Image Assurance feature as a contributing risk, even if you do not use the feature. If you are not using Image Assurance, the Cluster Security Score assumes a perfect score (100) for "High Risk Images" and "Unscanned Images" risks. However, Image Assurance is weighted at 50%; although you are not seeing the widest view of risk available without it, you can still make progress with the other 50% contributing risks. To use Image Assurance, see Image Assurance scanner.
-
Currently, the historical score graph does not properly display a single data point, which is the case when the dashboard first starts assessing your cluster. With time, the historical graph will properly display data.
-
You cannot customize the dashboard
Dashboard walkthrough
Security Posture Overview dashboard
The Security Posture Overview dashboard provides an overall view of a cluster’s risk. As a strategic dashboard, you typically won’t have the bandwidth to tackle everything at once, but with planning, you can achieve your goals over time.
Note that the dashboard reflects risk assessments related to build and deploy time only. Security events related to runtime threat defense features (DPI, container threat detection, WAF) are not included. To view threat security events, see the Security Events Management dashboard.
Updates to the dashboard
The Cluster Security Score (and the data used by the risk calculators) are updated once a day.
In the left navbar, go to: Dashboards, Security Posture.
Cluster security score
The Cluster Security Score measures the overall security posture of your Kubernetes cluster based on contributing risks (listed under the score).
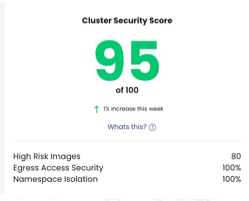
How the score is calculated
The cluster security score is a complex combination of cluster score, namespace score, and risk calculator scores (based on percentages and averages). It is calculated by taking the total risk score for the cluster (current and previous value) and subtracting it from 100. The higher the score, the better the cluster is doing.
Note also that the risk scores for egress access security and namespace isolation do not include misconfigurations.
Contributing risk types
Each risk type that contributes to the score is calculated and aggregated at two levels: for each namespace and each cluster.
| Risk | Enabled by default? | Score reflects… | Why it matters |
|---|---|---|---|
| High Risk Images | No | The number of images running in the namespace with High or Critical vulnerabilities. | Scanning images for known vulnerabilities is one of the most effective ways to prevent attackers from leveraging known exploits to gain access to systems and data. |
| Unscanned images | No | Images that have not been scanned. | Unscanned images can contain secrets, passwords, private keys, etc. and pose a risk. |
| Egress Access Security | Yes | The percentage of workloads that are communicating with endpoints external to the cluster that are not secured by network policy. | Implementing egress access controls helps mitigate the risk of unauthorized communication with malicious destinations, and helps prevent several phases of the MITRE Attack Matrix. |
| Namespace isolation | Yes | The percentage of egress and ingress network traffic to/from namespaces that are not secured by network policy. | Isolating namespaces enforces multi-tenancy in your cluster to reduce the impact of potential issues. It also improves security to prevent several phases of the MITRE Attack Matrix. |
About High Risk Images and Unscanned Images
These risks are associated with Image Assurance, an optional feature for scanning images for vulnerabilities If you are not using Image Assurance, the risk assessment displays a perfect 100 (maximum security). So your cluster security score will never drop below 50 out of 100. When you decide to use Image Assurance, your overall score will likely change.
Unscanned images are considered high risk until they are scanned.
How to remediate scores for high risk images
Use the Remediation panel in the Security Posture Overview dashboard to understand the recommended actions, then use the Image Assurance dashboard to address the issues.
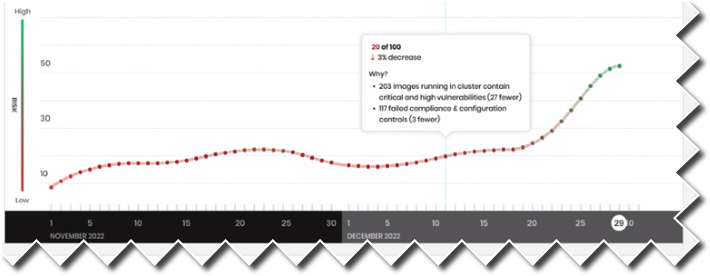
Historical graph
The historical graph is a time series of cluster risk scores. The historical scores are static (recorded once and do not change). Data starts to display in the graph approximately TBD days after you install a managed cluster.
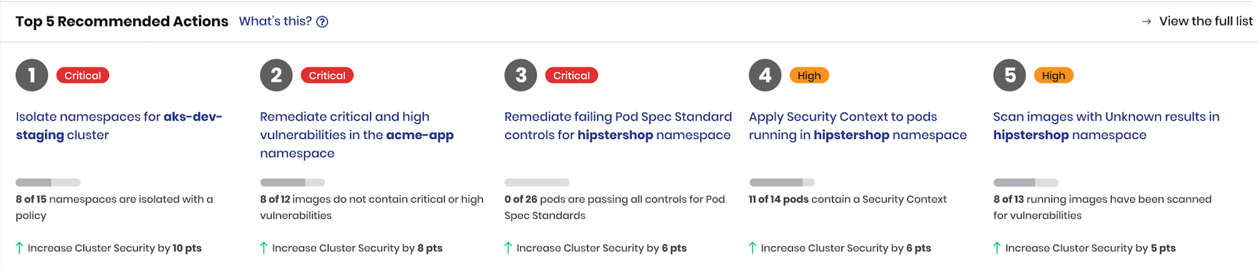
Top 5 recommended actions
The Recommended Actions panel is a prioritized list of actions you can take to improve your cluster security score; remediating the first recommendation in the list will improve your score the most.
A key mitigation control is Calico Cloud's automatic Policy recommendation, which is a staged network policy that teams can test and quickly enforce. Policy recommendations requires enabling, but no configuration.
Dismissing recommended actions
If you dismiss an action, the risk included in the action is ignored and will no longer affect the cluster security score. Although you can dismiss and revert a recommended action, Calico Cloud controls removing and updating existing actions.