Secure ingress access to a microservice or application
In this article you will learn how to create Calico Cloud policies that securely allow ingress access to a microservice or application.
- Ingress access to a microservice
- Ingress access to an application
Secure ingress access to a microservice
In this example, we have a microservices with four services (sv1, sv2, sv3, and sv4). Let's assume the following requirements:
- Everyone internal to the organization can access
svc1pods at TCP port 10001 svc1pods can accesssvc2at TCP port 10002svc3pods can access at TCP port 10003svc2pods can accessvc4at TCP ports 10004, 10005
Also, because svc1 pods pass through a trusted load balancer, we want to allow ingress traffic for the load balancer.
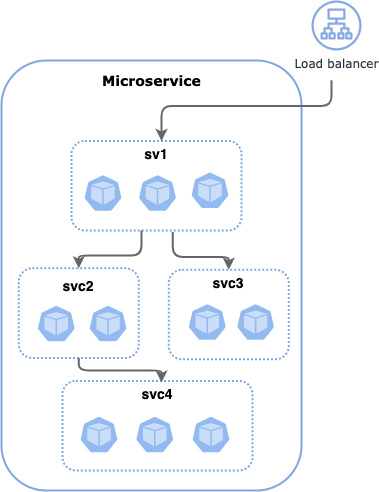
Let's start with securing ingress access to the trusted load balancer. We will use the Calico Cloud GlobalNetworkSet resource with cluster-wide scope to define the load balancer IP addresses; this allows the same trusted external endpoints to be used across multiple namespaces.
GlobalNetworkSet for load balancer
This GlobalNetworkSet contains the IP addresses for the trusted load balancer.
apiVersion: projectcalico.org/v3
kind: GlobalNetworkSet
metadata:
name: load-balancer
labels:
trusted-ep: "load-balancer"
spec:
nets:
# Modify the ip addresses to refer to the ip addresses of load-balancers in your environment
- 10.0.0.1/32
- 10.0.0.2/32
Next, we will create four network policies.
NetworkPolicy 1
This policy allows ingress from the trusted load balancer to pods in sv1.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app2-svc1
namespace: app2-ns
spec:
tier: application
order: 500
selector: (app == "app2" && svc == "svc1")
ingress:
- action: Allow
protocol: TCP
source:
selector: trusted-ep == "load-balancer"
destination:
ports:
- '10001'
types:
- Ingress
NetworkPolicy 2
This policy allows ingress access from sv1 pods to sv2 pods.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app2-svc2
namespace: app2-ns
spec:
tier: application
order: 600
selector: (app == "app2" && svc == "svc2")
ingress:
- action: Allow
protocol: TCP
source:
selector: svc == "svc1"
destination:
ports:
- '10002'
types:
- Ingress
NetworkPolicy 3
This policy allows ingress access from svc1 pods to svc3 pods.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app2-svc3
namespace: app2-ns
spec:
tier: application
order: 700
selector: (app == "app2" && svc == "svc3")
ingress:
- action: Allow
protocol: TCP
source:
selector: svc == "svc1"
destination:
ports:
- '10003'
types:
- Ingress
NetworkPolicy 4
This policy allows ingress access from svc2 pods to svc4 pods.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app2-svc4
namespace: app2-ns
spec:
tier: application
order: 800
selector: (app == "app2" && svc == "svc4")
ingress:
- action: Allow
protocol: TCP
source:
selector: svc == "svc2"
destination:
ports:
- '10003'
- '10004'
types:
- Ingress
Secure ingress access to an application
In this example, we have an application with frontend, backend, and a database. Let's assume the following requirements:
- Everyone internal to the organization can access the
frontendat TCP port 10001 frontendcan access thebackendat TCP port 10002backendcan access thedatabaseat TCP ports 10003, 10004
Also, because frontend pods pass through a trusted load balancer, we want to allow ingress traffic for the load balancer.
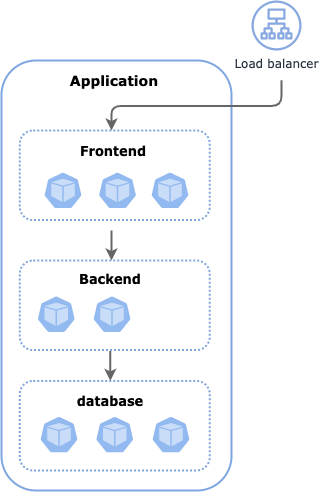
Let's start with securing ingress access to the trusted load balancer. We will use the Calico Cloud GlobalNetworkSet resource with cluster-wide scope to define the load balancer IP addresses; this allows the same trusted external endpoints to be used across multiple namespaces.
GlobalNetworkSet for load balancer
This GlobalNetworkSet contains the IP addresses for the trusted load balancer.
apiVersion: projectcalico.org/v3
kind: GlobalNetworkSet
metadata:
name: load-balancer
labels:
trusted-ep: "load-balancer"
spec:
nets:
# Modify the ip addresses to refer to the ip addresses of load-balancers in your environment
- 10.0.0.1/32
- 10.0.0.2/32
Next, we will create three network policies.
NetworkPolicy 1
This policy allows ingress from the trusted load balancer to pods in frontend.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app1-frontend
namespace: app1-ns
spec:
tier: application
order: 200
selector: (app == "app1" && svc == "frontend")
serviceAccountSelector: ''
ingress:
- action: Allow
protocol: TCP
source:
selector: trusted-ep == "load-balancer"
destination:
ports:
- '10001'
types:
- Ingress
NetworkPolicy 2
This policy allows ingress access from pods in the frontend to pods in the backend.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app1-backend
namespace: app1-ns
spec:
tier: application
order: 300
selector: (app == "app1" && svc == "backend")
serviceAccountSelector: ''
ingress:
- action: Allow
protocol: TCP
source:
selector: svc == "frontend"
destination:
ports:
- '10002'
types:
- Ingress
NetworkPolicy 3
This policy allows ingress access from pods in the backend to pods in the database.
apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: application.app1-database
namespace: app1-ns
spec:
tier: application
order: 400
selector: (app == "app1" && svc == "database")
serviceAccountSelector: ''
ingress:
- action: Allow
protocol: TCP
source:
selector: svc == "backend"
destination:
ports:
- '10003'
- '10004'
types:
- Ingress