Options for installing Calico Enterprise
Big picture
Understand the options for installing Calico Enterprise.
Value
Determine the right install method for your deployment, how to customize your installation configuration, and explains concepts important for integrating Calico Enterprise into your configuration management.
Concepts
API-driven installation
The Tigera Operator APIs (operator.tigera.io), let you define a Calico Enterprise cluster using declarative states. The APIs in the operator.tigera.io group define the desired state for your installation, and provide status reporting and visibility into the health of Calico Enterprise. The Tigera Operator makes sure the cluster’s state matches your desired state. These APIs can be configured at install-time, and can also be modified on a running cluster to adjust configuration.
Available APIs
Each API in the operator.tigera.io API group configures the installation of a different Calico Enterprise subsystem. The resources that you deploy and the settings you choose for each, depends on your cluster(s). For a detailed look at the available APIs, see the installation API reference.
| Resource | Description |
|---|---|
| Installation | The foundation of every deployment is the Installation resource. It deploys core networking and network policy enforcement features to the cluster, and is required for all other resources to function. |
| APIServer | Installs the Tigera API server, which enables access to the full set of Calico Enterprise APIs. |
| LogStorage | Configures installation of storage for Calico Enterprise flow and DNS logs. |
| LogCollector | Configures collection of those logs from the cluster, including optional configuration to backup logs in additional stores. |
| IntrusionDetection | Configures the Calico Enterprise intrusion detection feature. |
| Manager | Installs the Calico Enterprise web console. |
| ManagementClusterConnection | Configures a connection to the management cluster for managed clusters. |
| TigeraStatus | Displays conditions for a component (available, progressing, or degraded). |
| Compliance | Configures the Calico Enterprise compliance reporting feature (Optional). For managed clusters, ensure compliance reporting is enabled first on the management cluster. |
| PacketCaptureAPI | Configures the Calico Enterprise packet capture feature (Optional). |
Additional configuration
In addition to the above APIs, some product features are configured through additional Kubernetes Secrets and Kubernetes ConfigMaps. For details, see the relevant documentation for each feature.
Customize over time
The out-of-the-box Calico Enterprise installation gives you a working cluster with reasonable defaults with minimal post-installation tasks.
| Initial install | You get... |
|---|---|
| Cluster | A working cluster of Calico Enterprise nodes with verified connectivity. |
| Networking | Default networking implementation based on your provider and platform. Default IP pool/CIDR range. |
| Tiered network policy | Tiered network policy components. Existing Kubernetes clusters are put in default tier. Calico Enterprise components are secured with network policy. |
| User interface | the Calico Enterprise web console user interface (with a default of “no access outside the cluster”). |
| Logs and data | All nodes configured for log data collection using fluentdLog storage for a single node. One instance of Elasticsearch and Kibana. |
| Threat prevention and detection | Components and dashboards for tracing and blocking suspicious activity. |
| Compliance reporting | Components and dashboards to assess Kubernetes workloads and environments for regulatory compliance to enforce controls, and generate audit and evidence data. |
| Scaling | Built-in node scaling using Typha. |
You do not have to customize everything during initial install. As you progress through each stage of implementing Calico Enterprise leading to production (following diagram), you will gradually customize Calico Enterprise resources and automate cluster deployment. For example, when you move to 2 - Pre-production, you may switch from standalone clusters (default) to multi-cluster management for centralization and scaling.
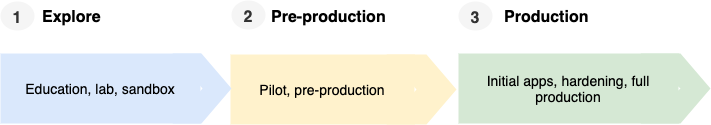
API-driven installation options
For most users, we recommend the standard installation, which uses a Kubernetes operator to guide and manage the installation. For exceptional circumstances, Calico Enterprise components can be installed using the following methods:
Install directly on non-cluster hosts
Although Calico Enterprise requires a Kubernetes control plane to function, you may want to install the node components on non-cluster hosts to consistently secure all of your infrastructure.
Install on Kubernetes using Helm
If your deployment requires Helm charts, we provide a helm chart that installs Calico Enterprise using the Tigera Operator. The Helm values.yaml includes sections that correspond directly to the operator.tigera.io APIs for installing the product. In the following example, the installation value is piped into the spec field of the installation API.
values.yaml
installation:
variant: TigeraSecureEnterprise
registry: gcr.io/mycorp
installation.yaml
apiVersion: operator.tigera.io/v1
kind: Installation
metadata:
name: default
spec:
variant: TigeraSecureEnterprise
registry: gcr.io/mycorp
Installation steps
The following table shows the conceptual stages of a Calico Enterprise install.
Details in the following steps will vary for platforms; for example, OpenShift automatically orchestrates the execution of the steps through tooling.
| Steps | Resources/files/APIs |
|---|---|
| 1 - Install the necessary APIs using CustomResourceDefinitions, and install the necessary operators | This step installs CustomResourceDefinitions (CRDs) into the cluster to enable the necessary API endpoints in the Kubernetes API server. It also installs the Tigera Operator and the Prometheus operator which implements those APIs. Tip: For most platforms, this step is accomplished by installing tigera-operator.yaml. However, note that OpenShift requires all resources to be in their own file, and so tigera-operator.yaml is split among many files for OpenShift installs. |
| 2 - Install any required Calico Enterprise resources | Depending on your cluster, you may want to configure certain features of Calico Enterprise at install-time. For example, you may require cluster-specific BGP configurations. You can create any install-time configuration using calicoctl. Tip: On OpenShift clusters, this is done automatically by placing configuration in a Kubernetes ConfigMap. |
| 3 - Install Calico Enterprise | Install Calico Enterprise by creating instances of the operator.tigera.io resources discussed above. The Tigera Operator reads this configuration and installs the necessary components, verifying that everything is working along the way. |
Frequently asked questions
Are new Calico Enterprise features always delivered in major or minor release of the Tigera Operator?
Usually, but not always. Sometimes new features are delivered in a patch version of the Tigera Operator.
How do I find the version of the Tigera Operator for troubleshooting?
kubectl exec -n tigera-operator -l name=tigera-operator -- operator --version
Which CLI do I use to customize and configure Calico Enterprise?
You can use kubectl for all resources in the operator.tigera.io/v1 API group.
For projectcalico.org/v3 APIs, you can use kubectl as long as the Tigera API server is running. Before the Tigera API server is running (for example, during product installation), you must use calicoctl to configure these APIs.
Next steps
- To get started with installation, see Install on clusters
- To upgrade from a non-operator installation method, see Upgrade