Stage, preview impacts, and enforce policy
Big picture
Stage and preview impacts on traffic before enforcing policy.
Value
Calico Enterprise staged network policy resources lets you test the traffic impact of the policy as if it were enforced, but without changing traffic flow. You can also preview the impacts of a staged policy on existing traffic. By verifying that correct flows are allowed and denied before enforcement, you can minimize misconfiguration and potential network disruption.
Concepts
About staged policies
The following staged policy resources have the same structure (i.e. the resource spec has the same fields) as their “enforced” counterpart.
- Staged global network policy
- Staged network policy
- Staged Kubernetes network policy
Review permissions
The default tigera-network-admin cluster role has the required permissions to manage the different enforced
and staged network policies. Adjust permissions for your environment. As with Calico Enterprise network policy and global network policies, the RBAC for Calico Enterprise staged network policy and staged global network policy is tier-dependent.
How to
- Create a policy recommendation
- Stage a policy
- Preview policy impact
- Enforce a staged policy
- Stage updates to an enforced policy
Create a policy recommendation
One of the first things developers need to do is secure unprotected workloads with network policy. (For example, by default, Kubernetes pods accept traffic from any source.) The Recommend policy feature allows developers with minimal experience writing policy to secure workloads.
Because Recommend policy looks at historical flow log entries that match your request, you should run your workloads for a reasonable amount of time to get "typical network traffic" for your application.
- In the left navbar, click Policies.
- Click Recommend a policy.
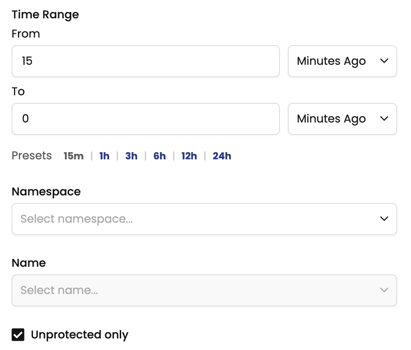
- Enter time range, Namespace, Name, and click Recommend.
- If relevant flow logs are found within the time range for the workload endpoint, click Preview to assess the impact of the recommended policy, or Stage.
Stage a policy
Stage a policy to test it in a near replica of a production environment. A best practice is to stage a policy before enforcing it to avoid unintentionally exposing or blocking other network traffic.
- In the left navbar, click Policies.
- In a tier, click Add Policy.
- Create your policy and click Stage to save and stage it.
Enforce a staged policy
- From Policies Board, click a staged policy.
- Click Edit policy, make changes and click Enforce. The staged policy is deleted and the enforced policy is created/updated (depending on whether it already exists).
Preview policy impact
The policy preview impact feature assesses traffic impact only on enforced staged policies.
- From the Policies Board, select a staged policy and click Edit policy.
- Make some edits and click Preview.
Stage updates to an enforced policy
- From the Policies Board, open an enforced policy.
- In View Policy, click Edit policy.
- Make your changes, and click Preview. Depending on the results, you can click Stage or Enforce.
You can also use custom resources to stage Kubernetes and Calico Enterprise policies, and apply them using kubectl. Here are sample YAML files.
Example: StagedGlobalNetworkPolicy
apiVersion: projectcalico.org/v3
kind: StagedGlobalNetworkPolicy
metadata:
name: default.allow-tcp-6379
spec:
tier: default
selector: role == 'database'
types:
- Ingress
- Egress
ingress:
- action: Allow
protocol: TCP
source:
selector: role == 'frontend'
destination:
ports:
- 6379
egress:
- action: Allow
Example: StagedNetworkPolicy
apiVersion: projectcalico.org/v3
kind: StagedNetworkPolicy
metadata:
name: default.allow-tcp-6379
namespace: default
spec:
tier: default
selector: role == 'database'
types:
- Ingress
- Egress
ingress:
- action: Allow
protocol: TCP
source:
selector: role == 'frontend'
destination:
ports:
- 6379
egress:
- action: Allow
Example: StagedKubernetesNetworkPolicy
apiVersion: projectcalico.org/v3
kind: StagedKubernetesNetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
role: db
policyTypes:
- Ingress
- Egress
ingress:
- from:
- ipBlock:
cidr: 172.17.0.0/16
except:
- 172.17.1.0/24
- namespaceSelector:
matchLabels:
project: myproject
- podSelector:
matchLabels:
role: frontend
ports:
- protocol: TCP
port: 6379
egress:
- to:
- ipBlock:
cidr: 10.0.0.0/24
ports:
- protocol: TCP
port: 5978
Additional resources
- Staged global network policy
- Staged network policy
- Staged Kubernetes network policy
- For details on how to configure RBAC for staged policy resources, see Configuring RBAC for tiered policy
- For details on staged policy metrics, see